DNS Hijacking: Navigating Cyber Threats Safely
Discover the growing menace of Ransomware-as-a-Service (RaaS) in cybersecurity. Uncover its profound impact, intricate business model, and vital defense strategies to thwart its devastating assaults. Explore actionable insights to mitigate risks, defend against evolving threats, and leverage cutting-edge intelligence for fortified protection against RaaS attacks.
Android Open-Source Project
Explore AOSP, Android's open-source foundation, free from proprietary elements. Delve into its components driving a diverse ecosystem, fostering innovation and customization. AOSP's open nature and ongoing evolution ensure a secure, adaptable base vital for Android's future advancements and user-driven modifications.
The Digital Operational Resilience Act (DORA)
DORA (Regulation EU 2022/2554) fills gaps in EU finance rules, enforcing comprehensive guidelines for operational resilience. It shifts focus from capital allocation to detailed measures covering ICT-related incidents: protection, detection, containment, recovery, and repair.
Ransomware-as-service: The growing threat that you can’t ignore
Discover the growing menace of Ransomware-as-a-Service (RaaS) in cybersecurity. Uncover its profound impact, intricate business model, and vital defense strategies to thwart its devastating assaults. Explore actionable insights to mitigate risks, defend against evolving threats, and leverage cutting-edge intelligence for fortified protection against RaaS attacks.
Spring Tool Suite(STS):Role Based User Aunthentication using STS
Discover role-based user authentication in Spring, covering registration, authentication, and JWT token-based authorization. Learn project flow, database setup, and security configurations. Integrate secure authentication into your Spring Application, tailoring admin and user pages to meet specific needs.
Enhancing Security with Two-Factor Authentication (2FA)
Uncover the potency of Two-Factor Authentication (2FA) in bolstering online security against modern cyber threats. Explore its types, advantages, implementation tips, and real-world success stories. Stay ahead in cybersecurity with insights into 2FA's future advancements. Elevate your defenses and shield crucial data with this comprehensive 2FA guide.
GraphQL: Transforming Modern Web Development
Explore the dynamic world of GraphQL and its impact on modern web development. Learn how GraphQL revolutionizes data fetching, enhances performance, and enables efficient API querying. Discover the benefits of GraphQL and how it can optimize your website's functionality and user experience.
Understanding Serverless Computing: A Game-Changer in Modern Tech
Discover serverless computing's transformative power in modern technology. Explore scalability, cost-effectiveness, and development speed. Learn leveraging cloud services, containers, and event-driven architecture for seamless operations. Unleash serverless computing's potential in digital endeavors today.
Exploring Microservices in Fullstack Development: An Overview
Delve into the world of microservices in full-stack development. Explore the fundamentals of this architectural style and how it enhances scalability, flexibility, and efficiency in application development. Gain insights into the benefits of incorporating microservices into your development process.
Cloud's Influence on Fullstack Dev: In-Depth Guide
Discover the profound impact of cloud computing on fullstack development. Learn how this innovative technology is reshaping the development landscape and optimizing efficiency. Explore the basics and benefits of integrating cloud computing into your fullstack projects.
The Unseen Threat: How Shadow IT Paves the Way for Ransomware Attacks
Understand the risks of shadow IT practices and their inadvertent facilitation of ransomware threats. Discover effective strategies to fortify your organizational defenses, mitigate vulnerabilities, and safeguard your data against the pervasive menace of shadow IT-induced ransomware infiltrations.
Unveiling the Differences Between Phishing and Spear Phishing: Know How to Protect Yourself
Discover the disparities between general phishing and targeted spear phishing, and fortify your defences against these prevalent cyber threats. Learn effective strategies to enhance your cyber resilience and safeguard your personal and organizational security effectively
Safeguarding Against Credential Dumping and Credential Reuse Attacks: A Comprehensive Guide
Learn about the critical significance of safeguarding credentials and the risks associated with credential reuse attacks. Explore effective strategies to fortify your digital security against credential dumping, and stay informed with expert insights and tips to protect your online presence effectively.
Safeguarding Your Data: The Perils of SQL Injection and Zero-Day Exploits
This blog delves into cybersecurity, spotlighting the critical risks of SQL injection and zero-day exploits. It highlights potential data breaches and system compromises. Offering defense strategies like security audits, intrusion detection, and staying updated, it advocates a proactive cybersecurity approach for safeguarding data and systems from these pervasive threats.
Protecting Your AWS Infrastructure: Understanding and Mitigating Cloud Cryptomining Threats
Cloud cryptomining exploits AWS resources to mine cryptocurrency, posing risks like system slowdowns and increased expenses. Protecting your AWS environment involves proactive measures: regular assessments, robust access controls, and vigilant monitoring. Staying updated on security measures and collaborating with experts ensures resilience against evolving threats, securing your cloud operations.
Decoding Cyber Security Threats: The Pitfall of Advanced Persistent Threats
Discover the ieats, mitigating risks with robust network monitoring and vigilant defense protocols. Stay ahead in the digital landscape with our comprehensive guide to cyber threat management.nsiious nature of Advanced Persistent Threats (APTs) and their reliance on Command and Control (C2) attacks. Learn how to fortify your cybersecurity strategy against these stealthy threats, mitigating risks with robust network monitoring and vigilant defense protocols. Stay ahead in the digital landscape with our comprehensive guide to cyber threat management.
Diffrence between == and === in kotlin
Explore the nuances of Kotlin's equality operators, understanding the distinction between Structural (==) and Referential (===) in this blog. Delve into their functionalities and impacts, exemplified through various scenarios and the role of implementing equals(). Discover the significance of converting classes to data classes in these operations.
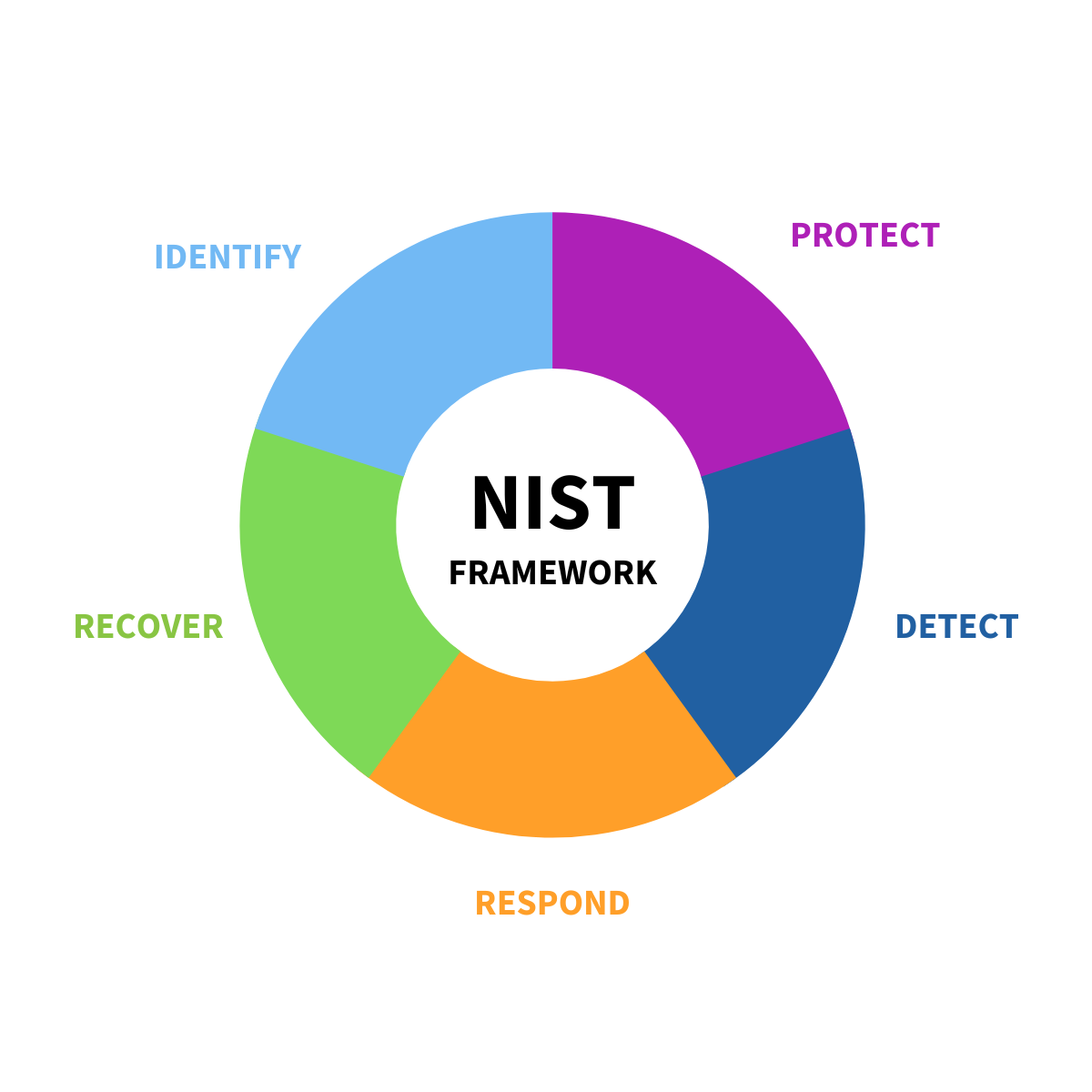
Strengthening cybersecurity governance with the NIST Framework
Explore the NIST Cybersecurity Framework and bolster your organization's cyber defenses. Learn how to leverage this structured approach to fortify governance, identify risks, protect assets, detect threats, respond efficiently, and recover post-incidents. Discover insights into proactive risk management in today's evolving threat landscape with itAgenturen's expert guidance.
Android: Health Connect API
Explore Health Connect, an Android API revolutionizing health data management. It unifies diverse health apps and devices, offering developers a simplified integration interface while granting users control over data access. Seamlessly access on-device health data, fostering a cohesive ecosystem for enhanced health and fitness experiences.